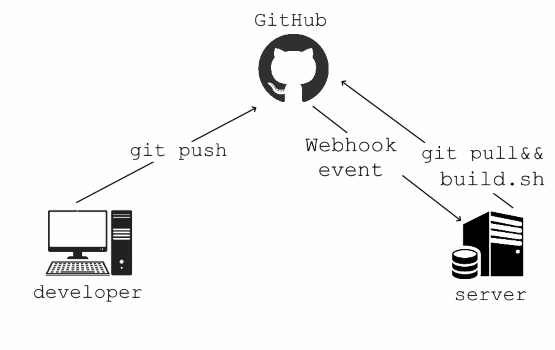
This is a small tool I have developed to setup simple continuous integration and continuous deployment for my GitHub projects. Of course, you can use AppVeyor, Travis CI or any other services to achieve the same result (or even more, these are really powerful tools). But if you just want to run a script when you push to master, this might be interesting for you. Webhook Runner for Github
It is running on your server and listening on the configured port (http://localhost:5000 by default) and has only one API endpoint POST /api/webhook. When it receives payload from GitHub, it will loop through a defined set of rules (defined in appsettins.json) and will execute command line from Execute property if ref value from payload matches Ref value from the rule and repository.url from the payload matches RepositoryUrl from the rule. If you configured Secret for the webhook, it will compare value for the X-Hub-Signature header with the WebHookSecret environment variable (can also be set in appsettings.config, but I would recommend keeping it as an environment variable).
Quick Start
You can download self-contained application for your platform:
- Linux-x64: https://github.com/drussilla/git-webhook-server/releases/download/0.4/linux-x64-v0.4.tar.gz
- Windows-x64: https://github.com/drussilla/git-webhook-server/releases/download/0.4/win-x64-v0.4.zip
Download:
wget https://github.com/drussilla/git-webhook-server/releases/download/0.4/linux-x64-v0.4.tar.gzMake it executable:
cd linux-x64
chmod +x git-webhook-server
Create file nano appsettings.json with rules:
{
"Logging": {
"LogLevel": {
"Default": "Information",
"Microsoft": "Warning",
"Microsoft.Hosting.Lifetime": "Information"
}
},
"AllowedHosts": "*",
"Rules": [
{
"Name": "master git-webhook-server",
"Ref": "refs/heads/master",
"RepositoryUrl": "https://github.com/drussilla/git-webhook-server",
"Execute": "run_in_tmux.sh"
}
]
}Node: Do not forget to replace values for RepositoryUrl and Execute properties.
Run:
./git-webhook-server --urls http://0.0.0.0:5000You can expose it to the outside world but I would recommend setting up nginx with SSL certificate (for example from Let's Encrypt) as a reverse-proxy in front of the WebHook Runner
If you decided to run it without nginx, do not forget to add a rule in the firewall (I hope you are using it) to allow access on the port 5000.
Running as a daemon
If you do not want to run it manually every time you reboot your machine or when the process is crashed, you can use surepvisor - system that allows its users to monitor and control a number of processes on UNIX-like operating systems.
Install
sudo apt-get install supervisorCreate a config file for your application
sudo nano /etc/supervisor/conf.d/git-webhook-server.confWith the following content:
[program:git-webhook-server]
command=su -c "/home/<username>/linux-x64/git-webhook-server --urls http://0.0.0.0:5000" <username>
directory=/home/<username>/linux-x64
autorestart=true
autostart=true
stdout_logfile=/home/<username>/linux-x64/out.log
stderr_logfile=/home/<username>/linux-x64/err.log
Note:: Replace <username> with the actual username.
Reload supervisor:
sudo supervisorctl reloadTo check the status of the app run:
sudo supervisorctl statusHow to configure webhook in GitHub
Configure webhook in GitHub repository:
- Set
Payload URLto the publicly visible URL of the Webhook Runner (e.g. http://example.com:5000/api/webhook) - Set
Content typetoapplication/json SSL verificationbased on your server config (I would strongly recommend setting up nginx with SSL certificate in front of the runner)- Set
Just the push event.because currently, this is the only supported event type (GitHub will getBadRequetresponse for any other event types) Activeshould be enabled
You can find more examples on GitHub