According to a Netcraft's study of the secured (SSL/TLS) sites they monitor, 95% of them are vulnerable to a simple man-in-the-middle attack because they didn't correctly implement HTTP Strict Transport Security (HSTS), a widely-supported security feature that prevents unencrypted HTTP connections to a server.
Let's see why it's happening and how we can make your website secure, again.
What is HTTP Strict Transport Security (HSTS)?
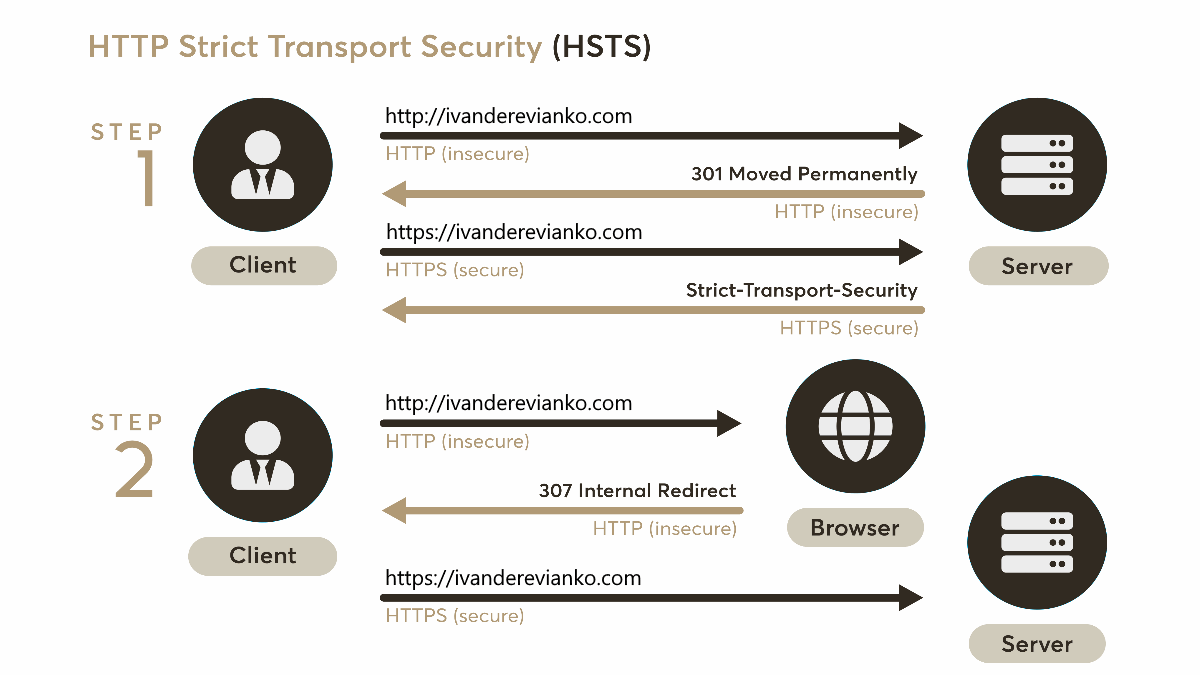
HSTS is a web security policy (RFC 6797) mechanism developed to protect websites against protocol downgrade attacks and cookie hijacking (wiki). When someone enters a website URL in the browser without http:// or https:// prefix or follows the http:// link, the initial request to the webserver is sent unencrypted. A correctly configured webserver should immediately redirect the user to the secured URL. Unfortunately, an attacker can set a man-in-the-middle (MITM) attack to intercept the first HTTP request.
HSTS is designed to help with this potential vulnerability by instructing the browser to always use a secured HTTPS connection to access the webserver (even if the user manually enters URL with the http:// prefix).
To enable this policy, a website should send the following HTTP response header:
Strict-Transport-Security: max-age=31536000When a browser receives this header from a secured website, it will access this website using HTTPS (SSL or TLS) for the next max-age seconds.
You can also specify this policy for all subdomains by including includeSubDomains directive to the response:
Strict-Transport-Security: max-age=31536000; includeSubDomainsMaking HSTS Stronger
A user is protected against HTTP interception after a browser has received STS header from the webserver, but what if the user visiting the website for the first time or after max-age seconds?
To fix this problem, Google maintains a "HSTS preload list". This list is distributed and included in most major browsers (Chrome, Firefox, Opera, Safari, IE 11 and Edge). The browser that access web sites in this list automatically uses HTTPS and refuses to access the site using HTTP. To add your site to this list it should send a bit different HSTS header back to the browser and include preload directive in the STS response:
Strict-Transport-Security: max-age=31536000; includeSubDomains; preloadAdding HSTS Response in NGINX
Adding HSTS header to the response in NGINX is quite simple. Add the following line to the server block in the website's config:
add_header Strict-Transport-Security "max-age=31536000; includeSubDomains; preload" always;The always parameter enables HTST header in all responses, including internally generated error responses.
After adding this line in the config do not forget to test configuration and reload nginx:
sudo nginx -t
sudo service nginx reloadNow your website is secure and ready to be submitted to the "HSTS preload list".